Price CRM software serves as a vital tool for businesses wishing to streamline their customer relationship management efforts. In today’s competitive landscape, understanding the pricing structures of various CRM solutions is essential for making informed decisions that align with organizational goals. From small start-ups to large enterprises, the right CRM software can enhance customer engagement and drive sales growth, making it an invaluable asset for any business.
As we delve into the various aspects of price CRM software, we will explore the range of options available, the features that distinguish them, and the factors that influence their pricing. This comprehensive overview aims to equip businesses with the knowledge necessary to select the most suitable CRM solution for their unique needs.
In today’s digital landscape, the importance of ensuring strong cybersecurity cannot be overstated. As technology continues to advance, so too do the tactics employed by cybercriminals, making it imperative for individuals and organizations to stay informed and vigilant. This article will delve into the critical aspects of cybersecurity, Artikel best practices for protecting sensitive information, and explore emerging trends that are shaping the future of cybersecurity.Cybersecurity refers to the measures taken to protect computer systems, networks, and data from theft, damage, or unauthorized access.
With the increasing reliance on information technology, the threats posed by cyberattacks have become more sophisticated and prevalent. Statistics reveal a troubling reality; cybercrime is expected to cost businesses around $10.5 trillion annually by 2025. This staggering figure highlights the urgency for comprehensive cybersecurity strategies.One of the most common forms of cyber threats is malware, which includes viruses, worms, and ransomware.
Malware can infiltrate systems, encrypt files, and demand a ransom for their release. The notorious WannaCry ransomware attack of 2017 serves as a cautionary tale, affecting more than 200,000 computers across 150 countries. This incident underlines the need for organizations to adopt robust security measures.Phishing is another prevalent tactic used by cybercriminals, wherein attackers deceive individuals into providing sensitive information, such as passwords or credit card details, by masquerading as trustworthy entities.

Phishing attacks can be executed through emails, texts, or even phone calls. The Federal Trade Commission (FTC) has reported that consumers lost approximately $1.9 billion to fraud in 2020, with phishing being a leading cause. To combat this, awareness and education are vital. Individuals should be trained to recognize red flags, such as suspicious email addresses, grammatical errors, and urgent calls to action.Moreover, the importance of using strong, unique passwords cannot be emphasized enough.
Weak passwords are often the first line of defense for cybercriminals. One effective strategy is to adopt a password manager that generates and stores complex passwords securely. Additionally, implementing two-factor authentication (2FA) provides an extra layer of security, requiring not only a password but also a second form of verification, such as a fingerprint or a one-time code sent to a mobile device.Organizations must also prioritize regular updates and patches for their software and hardware.
Cybercriminals often exploit known vulnerabilities in outdated systems to launch attacks. Keeping systems updated ensures that security vulnerabilities are addressed promptly, reducing the risk of exploitation. Furthermore, conducting regular security assessments and penetration testing can help identify weaknesses before they can be exploited by malicious actors.Data encryption is another fundamental aspect of cybersecurity. By encoding sensitive data, organizations can protect it from unauthorized access.
Even if a cybercriminal intercepts encrypted data, they will find it virtually useless without the decryption key. Implementing encryption protocols for data at rest and in transit is essential for safeguarding personal and proprietary information.The rise of remote work, accelerated by the COVID-19 pandemic, has further emphasized the importance of cybersecurity. As employees access company networks from various locations and devices, the attack surface has expanded, making organizations more vulnerable to cyber threats.
Virtual Private Networks (VPNs) can provide secure access to company resources, ensuring that data transmitted over public networks remains encrypted. Additionally, organizations should establish clear guidelines for remote work, including the use of personal devices and the handling of sensitive information.The Internet of Things (IoT) is another factor contributing to the complexity of cybersecurity. With an increasing number of devices connected to the internet, each additional device presents a potential entry point for cybercriminals.
Smart home devices, wearables, and industrial control systems must be secured to prevent unauthorized access. Organizations should enforce strict security protocols for IoT devices, including regular updates and strong authentication measures.Artificial intelligence (AI) and machine learning are also playing an increasingly prominent role in the field of cybersecurity. These technologies can analyze vast amounts of data in real-time, identifying unusual patterns and potential threats more effectively than human analysts alone.
AI-driven security solutions can enhance threat detection and response, offering organizations a proactive defense against cyberattacks.As we look to the future, emerging trends in cybersecurity will further shape the landscape. One such trend is the growing emphasis on privacy regulations and compliance. Laws such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) underscore the importance of protecting personal data and holding organizations accountable for data breaches.
Compliance with these regulations not only avoids legal repercussions but also enhances consumer trust.Additionally, the shift towards zero trust security models is gaining traction. Traditionally, perimeter-based security measures assumed that everything inside the network was safe. However, zero trust models operate on the principle of “never trust, always verify.” This approach requires continuous authentication and validation of users and devices, regardless of their location, significantly reducing the risk of breaches.In conclusion, the field of cybersecurity is dynamic and ever-evolving, requiring continuous vigilance and adaptation to new threats.
Organizations and individuals alike must remain proactive in their efforts to safeguard sensitive information. By implementing best practices, fostering awareness, and embracing emerging technologies, we can build a more secure digital environment. As we navigate the complexities of cybersecurity, it is essential to remember that security is not just a technical issue but a shared responsibility that requires collaboration across all levels of society.
Commonly Asked Questions
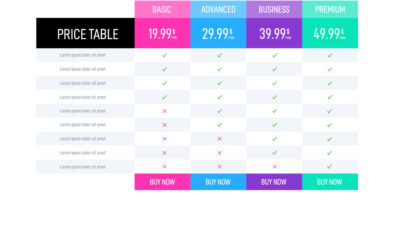
What factors influence the pricing of CRM software?

The pricing of CRM software can be influenced by various factors including the features offered, the number of users, the level of customization, and the type of support provided.
Are there free CRM software options available?
Yes, there are free CRM software options available, though they often come with limited features and support compared to paid versions.
How can a business determine the right CRM software for its needs?
A business can determine the right CRM software by assessing its specific requirements, considering factors such as company size, budget, and desired features.
Is it possible to integrate CRM software with other business tools?
Yes, many CRM software solutions offer integration capabilities with other business tools such as email marketing software, accounting systems, and project management tools.
How often should a business review its CRM software?
A business should review its CRM software periodically, especially after significant changes in operational needs or when new features become available.